How To Search Through Encrypted Documents
Compliance directives coupled with sophisticated cyber threats have led businesses to adopt a myriad of tactics to meet regulatory requirements and mitigate data security risks. As security practitioners implement these enhanced data security strategies, they are often faced with operational challenges when it comes to optimizing workflows and supporting business productivity. File encryption, which is a significant layer in any proper data security strategy, is often met with a common criticism - the inability to perform queries or searches of encrypted data without first decrypting it. For obvious reasons, this approach is neither practical nor secure.
A lesser known approach known as searchable encryption, enabled through multifactor encryption allows data to remain secure while balancing user productivity.
What is Secure Search?
Secure Search is a capability within Atakama's multifactor encryption solution. The Secure Search allows users to search through encrypted files without the need to decrypt the files or to generate an unencrypted search index, both of which present significant security risks.
How Does Secure Search Work?
To be able to search through encrypted files, Atakama creates an index for every file that it encrypts. The index itself is encrypted and appended to the encrypted file. Similar to the manner in which Atakama requires users to authorize the decryption of files, Atakama also requires users to authorize searches. When running a search, users enter their query in the Atakama search feature and approve the query with their mobile device. Any encrypted file with the specified search term will then be identified and located for the user.
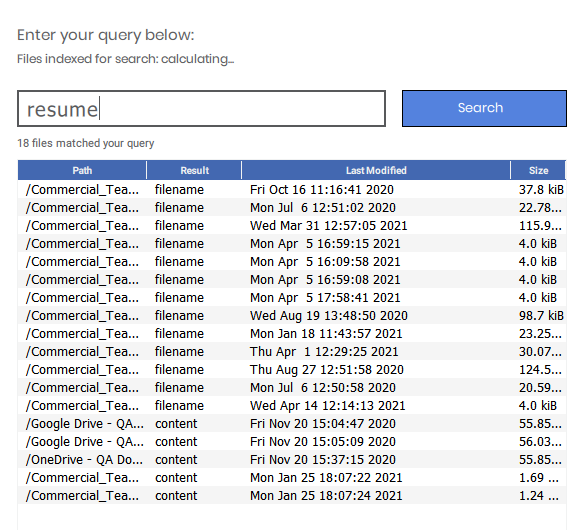
Here is a breakdown of Secure Search:
- Atakama creates an index for every file it encrypts, by encrypting each word in the file using techniques from PEKS and appending them to a blinded set.
- The index of encrypted words is appended to the encrypted file.
- Just as Atakama authorizes the decryption of files, it also now must authorize searches.
- When running a search, users enter their query and approve the query on their mobile device.
- The mobile device combines each word of the search query with the encryption key shards for each file.
- Atakama then uses the resulting combined information to securely locate files that contain the search terms.
To learn more about our searchable encryption features and how they can be used to protect your data, contact us today.
